The Dark Side of MCP: Security Risks and How to Regain Control of Agentic AI Workflows
The New Frontier: Agentic AI in the Enterprise
In the past year, enterprise AI has evolved from single-prompt interactions (“write an email,” “summarize this report”) to agentic workflows, where AI systems connect directly to company data, tools, and applications to execute multi-step tasks.
This shift has created massive productivity gains, but it’s also introduced a new, invisible attack surface. Sensitive data now moves between AI models, internal systems, and third-party tools faster than most organizations can monitor or control.
Security teams are suddenly responsible for a workflow channel they can’t see.
What Is MCP (Model Context Protocol)?
MCP, the Model Context Protocol, is an emerging open-source standard designed to bring order to this new complexity. It defines how AI models like Claude or Gpt-5 can securely interact with external systems, tools, and data sources.
Think of it as a common language that connects an AI model to applications, APIs, and company data.
What makes MCP so powerful is its simplicity. It’s remarkably easy to implement, which has made it the fastest and most widely adopted way to build agentic workflows today. Teams can connect AI models to real tools and data, turning ideas into working automations with no deep ML or systems knowledge required. This ease of use is what’s fueling MCP’s rapid rise across engineering and business teams.
The Dark Side of MCP: Security Risks
MCP is a huge leap forward, but it also opens the door to new security challenges. Without clear visibility into which MCP clients and servers are in use and how these systems connect, sensitive data can slip through the cracks or be misused. Some risks include:
- Workflow Hijacking: An attacker could exploit a prompt injection to make an AI agent perform unauthorized actions, like creating bogus Jira tickets or committing bad code.
- Credential Theft: A rogue MCP server could collect tokens or secrets during agent interactions.
- Tool Poisoning: Unsanctioned or modified tools might manipulate agent behavior or data integrity.
- Sensitive Data Exfiltration: Without content inspection, private data can leave the enterprise boundary through legitimate-looking workflows.
Recently, the first malicious MCP server was found stealing emails in a rogue postmark-MCP package.
Security leaders are right to be concerned here. This is a workflow channel that bypasses traditional DLP, CASB, or endpoint protections.
Introducing Harmonic’s MCP Gateway
Today, we’re launching the Harmonic MCP Gateway: the Control Plane for Agentic Workflows.
MCP Gateway is a lightweight, developer-friendly solution that gives organizations complete visibility and control over their MCP ecosystem. It transparently inspects all MCP traffic, allowing security teams to:
- Discover MCP clients and servers in use across the organization.
- Enforce controls to block risky actions or unapproved clients/servers.
- Protect sensitive data using Harmonic’s industry-leading detection models to prevent the exfiltration of critical intellectual property and other sensitive information.
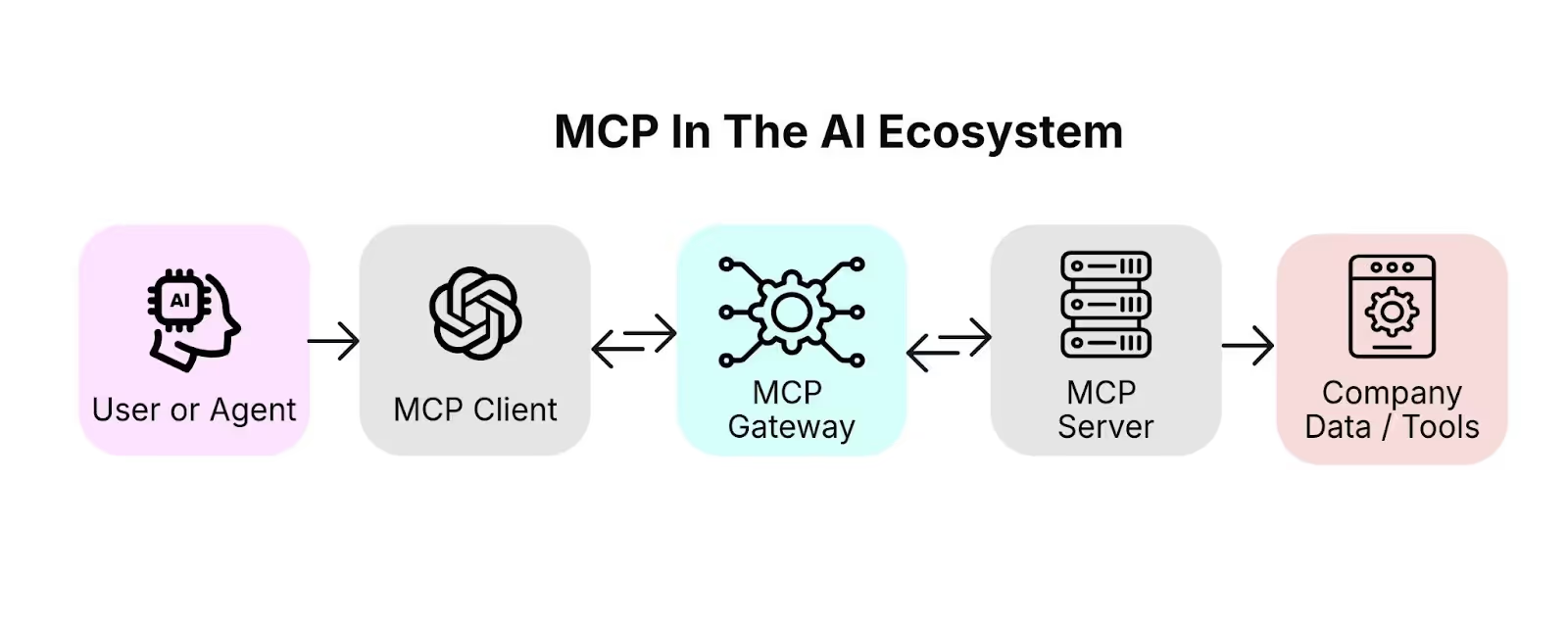
Rather than lock AI down, we want to enable safe AI adoption. Here’s a quick look at how it works:
Looking Ahead
AI adoption is accelerating, and security teams need a way to keep pace, not by blocking innovation, but by governing it intelligently.
Harmonic’s MCP Gateway helps to bridge that gap, giving organizations the visibility and control to move from reactive alerting to proactive prevention without slowing down your developers or business teams.
We’ll be sharing more insights on agentic AI and the MCP Gateway in upcoming posts. Stay tuned—and in the meantime, explore how Harmonic’s MCP Gateway can help secure your AI workflows: https://www.harmonic.security/get-demo




